
Cybersecurity Awareness Training
Help your employees strengthen your defenses against evolving digital risks while maintaining operational resilience.
Course description
Traliant’s Cybersecurity Awareness training is a 30-minute course that helps employees understand how to apply cybersecurity hygiene to protect an organization’s digital infrastructure while ensuring compliance with relevant laws, industry standards and company policies.
Enhance your training with Traliant’s Phishing Simulation, giving employees a practical, hands-on experience to improve their ability to spot phishing threats.
Short, engaging 2-minute microlearning courses are also available to reinforce key cybersecurity topics throughout the year. Topics include AI-enabled threats, social engineering, internet security, physical threats and insider threats.
ONLINE TRAINING
Cybersecurity Awareness Training

The course covers these topics and more:
- Phishing awareness
- Social engineering
- Common security threats
- Internet security
- Physical security
- Insider threats
- Anti-malware
- Multi-factor authentication
- AI enabled cyber threats
- Deepfakes
- Password management
- Reporting data breaches
THE TRALIANT DIFFERENCE
Compliance you can trust.
Training you will love.

Legal expertise
Our in-house legal team monitors the latest laws, rules and regulations, so you don't have to. You can rest assured that our courses are continuously compliant.

Brilliant training
Take your training from boring to brilliant. With cinematic-quality videos produced by our Hollywood-based team, your employees will love our customizable, interactive, story-based training.

Valued partnership
Our main focus? It’s all about making your job easier. We do that with unmatched responsiveness and seamless deployment, dedicated to driving your success.

Meaningful impact
We don’t just deliver brilliant training, we help you create meaningful impact by broadening your employees' perspectives, achieving compliance and elevating culture.
KEY FEATURES
Why you'll love our training
It’s time to embrace a new era of online training with a valued partner who will ensure seamless implementation to fit your exact, a truly enjoyable learning experience and courses with continuous compliance you can trust.
Compliance expertise
Traliant's in-house legal expertise ensures training is accurate and kept up-to-date with any regulatory changes.
Accessible to users with disabilities
Traliant provides an inclusive experience for all users, including those with disabilities, by going beyond Section 508-C standards and offering WCAG 2.1/2.2 AA.
Story-based learning
Our story-based approach blends leading instructional design with Hollywood talent to produce engaging, interactive and nuanced training.
Course administration
Traliant makes it simple to roll out training to your workplace and provide technical support directly to your employees at no additional cost.
Course customizations
Tailor courses to include your logo, relevant policies, workplace images, and more. Traliant can even customize the course with scenarios that take place in your own workplace environment.
Translations
Training is available in English, Spanish and is supported in over 100 languages.
COMPLIANCE EXPERTISE
Your partner in training compliance

Uniquely qualified in-house compliance team
Our exceptional in-house Compliance Advisory Team is led by Michael Johnson, Chief Strategy Officer and former U.S. Department of Justice attorney who has provided training and guidance to organizations like the Equal Employment Opportunity Commission, Google, the United Nations, and the World Bank.

Keeping you compliant, effortlessly
Keeping up with the complex web of employment laws — especially if your workforce spans multiple states — can be tricky. That’s why we offer a streamlined training solution that ensures you stay compliant with federal, state, and local regulations, so you can focus on what matters most: your team.

Simplifying your policies and handbooks
Crafting an employee handbook that meets legal standards can be daunting. Let us ease the burden. We help you navigate regulatory changes to ensure your policies and handbooks not only comply with the law but also reflect industry best practices.
What to consider when choosing the most effective Cybersecurity Awareness training
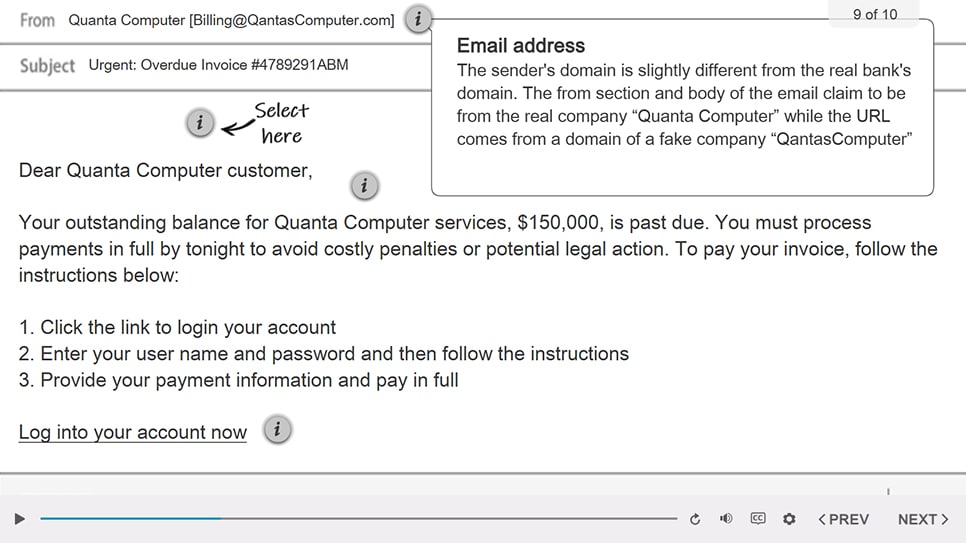
- Prevent cyberattacks: Training helps employees identify and avoid potential threats, such as phishing scams and malware.
- Protect sensitive information: Training helps employees understand the importance of protecting sensitive data and to follow best practices for handling and storing this information.
- Create a culture of cybersecurity: Training promotes a culture where everyone understands their role in protecting the organization's digital assets.
- Empower employees: Training provides employees with the knowledge they need to make informed decisions about their online behavior and to understand how to protect themselves and the company.
- Strengthen your cybersecurity posture: Training helps to build a strong cybersecurity culture, making it more difficult for cybercriminals to succeed.
- Reduce the risk of costly data breaches: Data breaches can have a significant financial and reputational impact on organizations. Training can help to minimize these risks.
- Annual Comprehensive Training to ensure employees understand the latest threats.
- Quarterly refresher or microlearning courses to reinforce key concepts in small, digestible sessions.
- Ongoing phishing simulations to test employees in real-world scenarios and help them recognize social engineering attacks.
Regular training ensures employees stay informed about new threats and develop a security-first mindset.
- Improving retention – small, digestible lessons help employees retain information better.
- Reducing disruption – employees can complete training in a few minutes, minimizing impact on productivity.
- Enhancing engagement – interactive and scenario-based microlearning keeps employees interested.
Microlearning ensures that cybersecurity awareness is reinforced throughout the year without overwhelming employees.
- Identifying vulnerabilities – employers can pinpoint employees who need additional training.
- Providing hands-on experience – employees practice spotting and reporting phishing attempts in a controlled environment.
- Reinforcing training concepts – repetition helps employees develop a habit of carefully scrutinizing emails and links before clicking.
- Measuring training effectiveness – organizations can track performance and adjust training accordingly.
By simulating real-world phishing attacks, businesses can proactively address weaknesses before they lead to security breaches.
- Cyber threats constantly evolve – new hacking techniques and vulnerabilities emerge regularly.
- Employees need regular reinforcement – periodic training helps reinforce best practices and develop lasting cybersecurity habits.
- Cyber risks are ever-present – cybercriminals continuously attempt attacks so employees must always remain vigilant.
- Compliance requirements – many industries require periodic cybersecurity training to meet regulatory standards.
A structured, ongoing training strategy – enhanced with phishing simulations and microlearning courses – helps organizations maintain a strong security culture and reduce the risk of cyber threats.




